Risk Management Enterprise for Beginners
Table of ContentsAn Unbiased View of Risk Management EnterpriseRisk Management Enterprise - TruthsThe 45-Second Trick For Risk Management EnterpriseHow Risk Management Enterprise can Save You Time, Stress, and Money.Risk Management Enterprise Can Be Fun For AnyoneRisk Management Enterprise Things To Know Before You Get ThisNot known Facts About Risk Management Enterprise
Here are several of its crucial functions that centers have to recognize. Take an appearance. Real-Time Danger Evaluations and Reduction in this software program enable organizations to continually check and assess threats as they progress. This feature leverages real-time information and automatic analysis to recognize prospective risks promptly. As soon as dangers are determined, the software program facilitates immediate mitigation actions.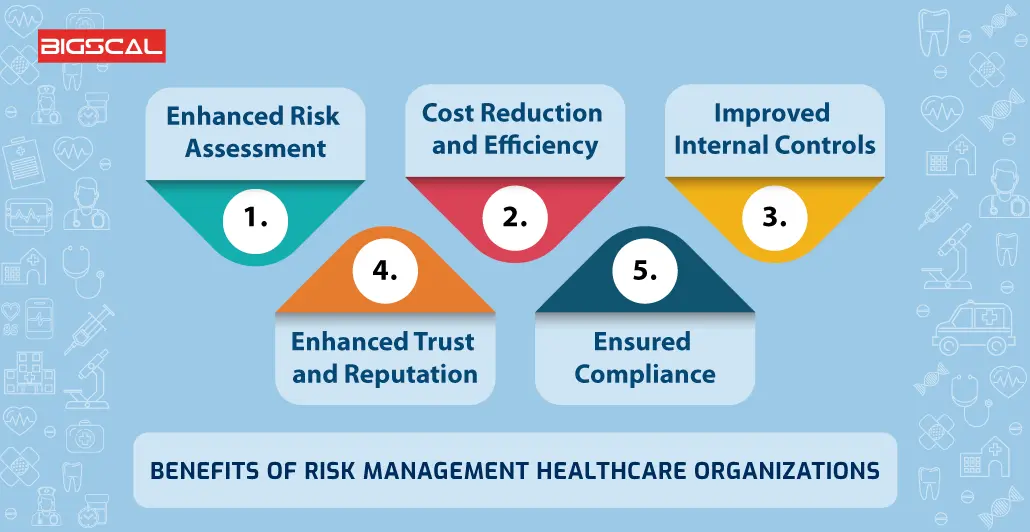
KRIs address the problem of inconsistent or uncertain threat assessment. They resolve the challenge of recurring threat management by offering tools to check threats continuously. KRIs improve protection risk oversight, making certain that potential threats are identified and taken care of successfully. The task of risk monitoring must not be an obstacle. Consequently, companies must rely upon an excellent and innovative threat monitoring software.
Some Known Factual Statements About Risk Management Enterprise
IT take the chance of management is a part of venture risk management (ERM), designed to bring IT take the chance of according to an organization's threat hunger. IT risk management (ITRM) incorporates the plans, procedures and technology necessary to minimize threats and vulnerabilities, while keeping compliance with suitable regulatory demands. Furthermore, ITRM seeks to limit the consequences of harmful occasions, such as safety and security breaches.
While ITRM structures provide helpful support, it's very easy for IT teams to experience "structure overload." Veronica Rose, ISACA board director and an info systems auditor at Metropol Corp. Ltd., suggests the usage of a combination of structures to achieve the very best outcomes. The ISACA Risk IT framework aligns well with the COBIT 2019 framework, Rose said.
Venture Risk Administration Software Program Advancement: Conveniences & Qualities, Cost. With technical developments, threats are continuously increasing. That being claimed, companies are most likely to encounter obstacles that affect their funds, operations, and online reputation. From swiftly rising and fall markets to governing adjustments and cyber dangers, services navigate via a frequently transforming sea of threats.
The smart Trick of Risk Management Enterprise That Nobody is Discussing
In this blog site, we will study the globe of ERM software, exploring what it is, its advantages, features, etc to make sure that you can build one for your service. Venture Threat Management (ERM) software application is the application program for preparation, routing, arranging, and controlling company tasks and simplifying risk management processes.
With ERM, organizations can make informative choices to boost the total strength of the business. Read: ERP Application Advancement Devoted ERM systems are crucial for businesses that consistently deal with vast amounts of sensitive information and several stakeholders to authorize critical decisions. Some industries where ERM has ended up being a standard system are health care, financing, construction, insurance coverage, and infotech (IT).
: It is demanding for any type of enterprise to undergo a comprehensive audit. It can be stayed clear of by utilizing the ERM software system. This system automates law compliance monitoring to keep the organization safe and secure and compliant. Apart from that, it additionally logs and classifies all the data in the system making it less complicated for auditors to examine procedures much faster.
The Single Strategy To Use For Risk Management Enterprise
You can also link existing software program systems to the ERM through APIs or by including information by hand. Companies can utilize ERM to review threats based upon their potential impact for better risk management and mitigation.: Adding this feature allows users to get real-time notifications on their devices regarding any type of threat that might happen and its influence.
Instead, the software program enables them to set limits for different procedures and send press notices in situation of feasible threats.: By integrating data visualization and reporting in the customized ERM software program, organizations can gain clear insights about danger patterns and performance.: It is required for organizations to abide by sector conformity and regulatory criteria.

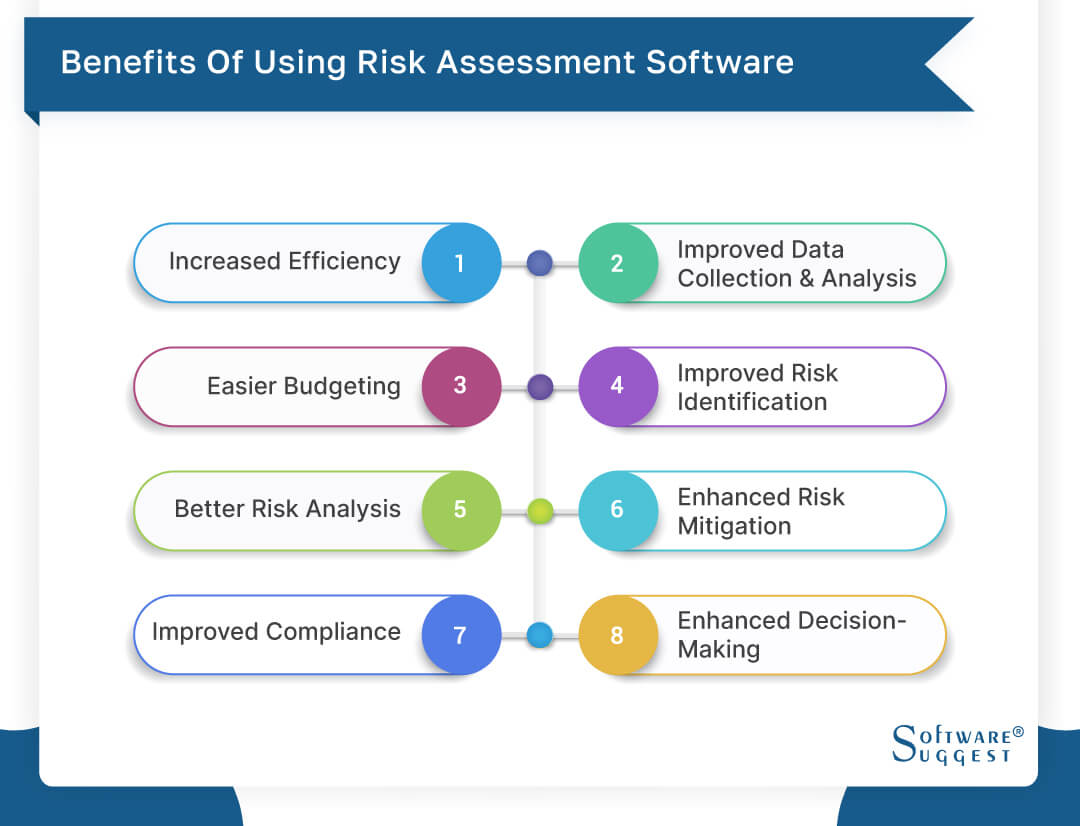
These systems allow companies to implement best-practice risk management procedures that straighten with sector criteria, supplying an effective, technology-driven technique to determining, examining, and mitigating threats. This blog site discovers the advantages of automated risk administration tools, the areas of threat monitoring they can automate, and the value they give an organization.
Some Known Factual Statements About Risk Management Enterprise
Teams can establish forms with the pertinent fields and quickly produce different forms for different danger types. These danger analysis types can be distributed for conclusion via automated process that send notices to the appropriate staff to complete the forms online. If kinds are not completed by the deadline, then chaser emails are automatically sent by the system.
The control tracking and control testing procedure can likewise be automated. Firms can use computerized workflows to send out regular control test notices and team can go into the results by means of online types. Controls can additionally be checked by the software by establishing guidelines to send out signals based upon control data kept in various other systems and spreadsheets that is pulled right into the platform via API assimilations.
Risk monitoring automation software program can also support with danger reporting for all degrees of the business. Leaders can see records on danger direct exposure and control efficiency through a range of reporting outputs consisting of static records, Power BI interactive reports, bowtie evaluation, and Monte Carlo simulations. The ability to draw actual time reports at the touch of a switch reduces out difficult information adjustment tasks leaving danger teams with even more time to assess the data and recommend business on the best strategy.
The demand for effective has actually never ever been a lot more pressing. Risk Management Enterprise. Organizations operating in competitive, fast-changing markets can not afford hold-ups or inadequacies in attending to possible dangers. Conventional threat administration making use of hand-operated spreadsheet-based processes, while acquainted, typically lead to fragmented information, time-consuming reporting, and a raised likelihood of human mistake. Automating the danger monitoring procedure with software program addresses these drawbacks.
The 6-Minute Rule for Risk Management Enterprise
This ensures danger signs up are constantly present and lined up with business objectives. Conformity is another crucial driver Risk Management Enterprise for automating threat monitoring. Requirements like ISO 31000, CPS 230 and COSO all supply support around danger management finest practices and control structures, and automated danger administration tools are structured to straighten with these requirements aiding firms to meet most generally utilized risk monitoring requirements.
Try to find risk software systems with an authorizations power structure to quickly set up process for danger rise. This performance enables you to tailor the view for each and every individual, so they only see the data relevant to them. Make certain the ERM software supplies user tracking so you can see that entered what data and when.
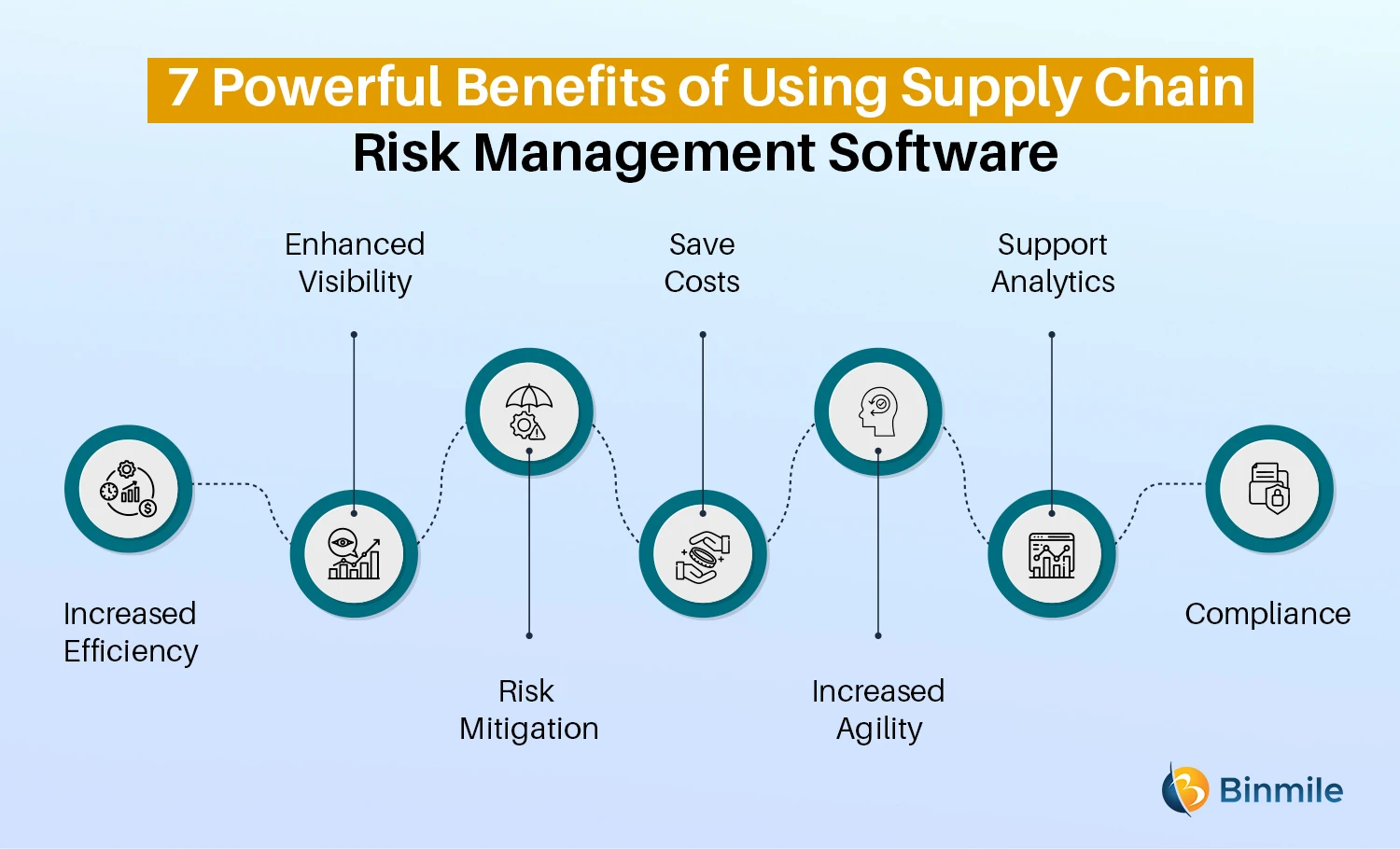
Select a cloud-based platform to make certain the system receives routine updates from the supplier adding brand-new functionality. Seek devices that supply project danger monitoring capabilities to manage your tasks and portfolios and the associated risks. The benefits of adopting danger management automation software prolong much beyond performance. Services that incorporate these services right into their ERM technique can anticipate a host of substantial and intangible.
Risk Management Enterprise Can Be Fun For Everyone
While the instance for automation is engaging, carrying out a threat monitoring system is not without its difficulties. To conquer the challenges of threat monitoring automation, organizations should invest in information cleansing and governance to make certain a solid structure for carrying out an automated platform.
Automation in risk monitoring encourages services to transform their approach to risk and build a more powerful foundation for the future (Risk Management Enterprise). The question is no more whether to automate threat monitoring, it's just how quickly you can start. To see the Riskonnect in activity,
The solution usually hinges on just how well risks are anticipated and taken care of. Task management software application serves as the navigator in the tumultuous waters of job execution, offering devices that determine and evaluate threats and devise methods to mitigate them properly. From real-time data analytics to thorough danger monitoring control panels, these devices offer a 360-degree sight of the job landscape, making it possible for job managers to make enlightened choices that keep their tasks on track and within budget plan.